Cloud Strategy
We accomplish what is important to you, bringing every organizational need to a tailor-fit cloud strategy that ensures scalability, flexibility and mobility of all your business and IT infrastructure applications
Business transformation for end-to-end service delivery
Our enterprise cloud services are designed to meet the requirements of diverse enterprise applications including sensitive and critical applications of the business. Our comprehensive cloud strategy provides the world-class tools and resources, loaded with myriad features for achieving organizational objectives of your workload and application portfolio. Our cloud strategy improves your business agility, future flexibility and reduce the exposure of security risks.
We offer three kinds of cloud services such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Also, each of these services can be deployed by private, public and hybrid cloud versions. We identify and understand the detailed workings of your business, assess specific requirements to be transformed into the cloud, build right platforms in transition plan, and define a cloud strategy to meet current and future business needs.
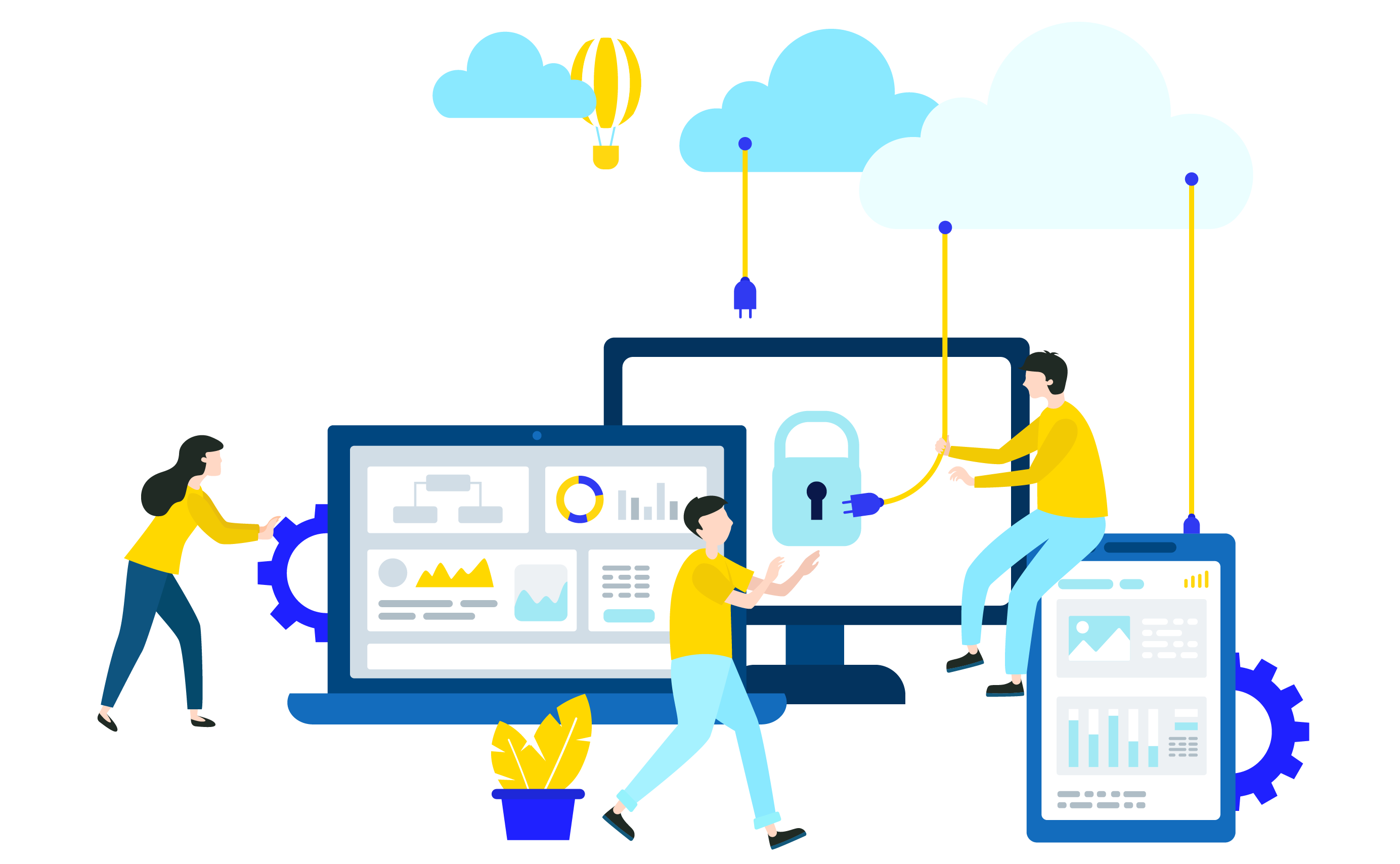
Flexible Deployment
We provide the complete deployment choice of the cloud (such as private, public and hybrid) and preferred comprehensive services (such as IaaS, SaaS, PaaS, and DaaS) to support diverse business requirements like migrating enterprise workloads, hosting business and collaboration applications, provisioning infrastructure management, etc.
Complete Integration
Our proven integrated cloud solutions help enterprises to integrate traditional applications and other workloads across multiple environments with cloud resources to ensure process coordination and data synchronization in real-time, supporting both cloud-to-legacy and cloud-to-cloud integration.
Security & Regulatory Compliance
Our custom governance policies, security practices and monitoring techniques can help you reduce the risks associated with applications, identities and proprietary data on the cloud. We provide the expertise to ensure the extensive protection for every cloud deployment and automate the security updates and actionable recommendations to reduce cyber threats and risks.
Our Cloud Deployment Models and Services
Our Leaders
Guide, Integrate, Validate & Manage
We offer 24x7x365 monitoring and support for DRaaS key services, including initial deployment, testing, failover and failback.
Blogs
Baseline Cybersecurity Requirements for Federal Contractors
Federal contractors are held to extremely high information security standards. With the recent introduction of new “Basic Safeguarding” standards for contractor information systems
Cryptocurrency Mining Malware Abuses 4000 Websites
Security Researcher, Scott Helme, first found malware that leveraged the victims’ devices to generate the cryptocurrency Monero by performing complex, CPU-intensive calculations, a mathematical process known as “mining” that’s used to create some cryptocurrencies.
The Future of Security Is Already Here
This blog is intended to share new ideas, insight and possibilities. This is not about what we already know. We know there is a rise in security threats and attacks.
We Are With You Every Step of the Way
Our engineers and consultants will setup, monitor, and maintain the software with aggressive SLAs and guarantee fundamental access never fails. We will even strategically align future software integration with our own software provision, our priority furnishing a secure system with effortless controls.
.png)

.png)
 (1).jpg)






